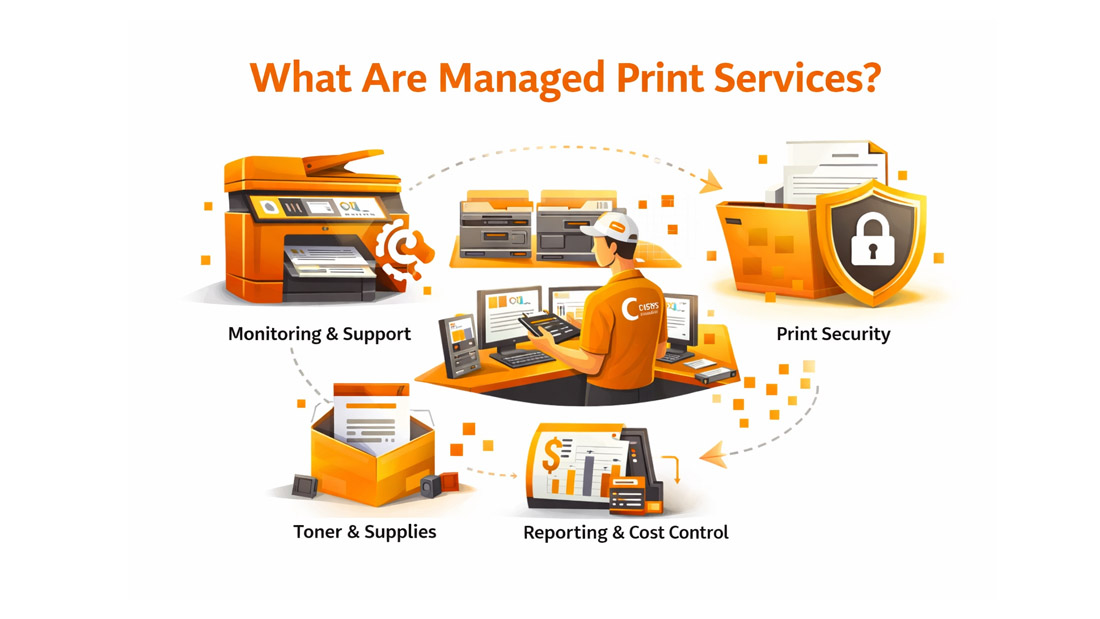
Achieving Cyber Security Compliance in the Auto Industry
October 25, 2022
Go back to "News & Updates"

Most business owners assume that cyber security compliance regulations apply primarily to financial institutions or perhaps even medical offices. But the truth is that hackers don’t really care what industry you’re in, so long as you have personal data in your possession.
The auto industry is no exception. The purchasing, selling, and repairing of cars requires a substantial exchange of information between the customer and the provider, which can be very attractive to identity thieves or other nefarious individuals.
For this reason, business owners in the auto industry will be required to comply with the Gramm-Leach Bliley Act (GLBA), a set of regulations meant to protect the consumer as they provide their personal information to businesses to obtain services or goods. And time is running out to be up to date with compliance. The regulations must be met by early December 2022.
The following is an overview of GLBA, its requirements, and what steps you need to take to keep your information safe and keep your business compliant. If upon review you feel as though these requirements are either beyond or bandwidth or level of technical skill, there are services, like Klipsys Technologies, that can handle the process from start to finish.
DEFINITION OF GLBA COMPLIANCE
The Gramm-Leach-Bliley Act (GLB Act or GLBA) is also known as the Financial Modernization Act of 1999. It is a United States federal law that requires financial institutions to explain how they share and protect their customers’ private information. To be GLBA compliant, financial institutions and other businesses handling personal information must:
- Communicate to their customers how they share the customers’ sensitive data
- Inform customers of their right to opt out if they prefer that their personal data not be shared with third parties
- Apply specific protections to customers’ private data in accordance with a written information security plan created by the institution
The revised rules became effective as of January 2022. Luckily, the Federal Trade Commission (FTC) is not enforcing the rules revisions until December 9th of 2022. But that doesn’t give businesses much time if they haven’t started putting a plan in motion.
The primary data protection implications of the GLBA are outlined in its Safeguards Rule, with additional privacy and security requirements issued by the FTC’s Financial Privacy Rule, created under the GLBA to drive the implementation of GLBA requirements. The GLBA is enforced by the FTC, the federal banking agencies, and other federal regulatory authorities, as well as state insurance oversight agencies.
In order to achieve GLBA compliance, the Safeguards Rule requires that financial institutions and other applicable businesses pay special attention to employee management and training, information systems, and security management in their information security plans and implementation
The main focus of the GLBA is to expand and tighten consumer data privacy safeguards and restrictions. The primary concern, related to the GLBA, of IT professionals and businesses, is to secure and ensure the confidentiality of customers’ private and financial information. Maintaining GLBA compliance is critical for any financial institution, as violations can be both costly and detrimental to continued operations. However, by taking steps to safeguard nonpublic personal information (NPI) and comply with the GLBA, organizations will not only benefit from improved security and the avoidance of penalties, but also from increased customer trust and loyalty.
3 CRITICAL RULES TO UNDERSTAND GLBA
Each of these three measures is designed to inform and guide organizations covered by the legislation about:
- The data types that are required to be protected
- Specific measures expected from the bill
- Preventing and lessening opportunities for unauthorized access
Below is a brief description of each of those three parts include in the GLBA
Financial Privacy Rule: A company that is either a “financial institution” or receives “NPI” regarding consumers from a financial institution must adhere to the privacy rule of the GLBA. This rule covers most personal information (eg, name, date of birth, Social Security number, etc.) as well as transactional data (eg, card, bank account numbers, etc.). It also covers private information you may acquire during a transaction (a credit report, for instance). The FTC has a page detailing every aspect of the privacy rule, right here
Safeguards Rule: This rule ensures that those under the jurisdiction of the GLBA have specific means to protect private information. According to the text of the rule itself, GLBA adherents must have “the administrative, technical, or physical safeguards you use to access, collect, distribute, process, protect, store, use, transmit, dispose of, or otherwise handle customer information.” Many of these techniques are outlined in the text as well.
Notable requirements include:
- Employee training
- Proper software
- Testing and monitoring of vulnerabilities
Pretexting Provisions: In addition to protecting NPI, organizations that fall under the GLBA must also take measures to detect and prevent as many instances of unauthorized access as possible. There are a number of nefarious scams trying to access personal data by phone, email, or even in person. Pretexting provisions aim to mitigate this data loss and protect more consumers.
HOW GLBA COMPLIANCE WORKS
The GLBA requires that financial institutions act to ensure the confidentiality and security of customers’ NPI. NPI includes Social Security numbers, credit and income histories, credit and bank card account numbers, phone numbers, addresses, names, and any other personal customer information received by a financial institution that is not public. The Safeguards Rule, as discussed earlier, states that financial institutions must create a written information security plan describing the program to protect their customers’ information. The information security plan must be tailored specifically to the institution’s size, operations, and complexity, as well as the sensitivity of the customers’ information. According to the Safeguards Rule, covered financial institutions must implement a reasonable information security program, which should model and incorporate the following guidelines:
GUIDELINES
a. Designate a Qualified Individual to implement and supervise your company’s information security program. The Qualified Individual can be an employee of your company or can work for an affiliate such as Klipsys Technologies. The person doesn’t need a particular degree or title. What matters is real-world know-how suited to your circumstances. The Qualified Individual selected by a small business may have a background different from someone running a large corporation’s complex system. If your company brings in a service provider to implement and supervise your program, the buck still stops with you. It’s your company’s responsibility to designate a senior employee to supervise that person. If the Qualified Individual works for an affiliate or service provider, that affiliate or service provider also must maintain an information security program that protects your business.
b. Conduct a risk assessment. You can’t formulate an effective information security program until you know what information you have and where it’s stored. After completing that inventory, conduct an assessment to determine foreseeable risks and threats – internal and external – to the security, confidentiality, and integrity of customer information. Among other things, your risk assessment must be written and must include criteria for evaluating those risks and threats. Think through how customer information could be disclosed without authorization, misused, altered, or destroyed. The risks to information constantly morph and mutate, so the Safeguards Rule requires you to conduct periodic reassessments in light of changes to your operations or the emergence of new threats.
c. Design and implement safeguards to control the risks identified through your risk assessment. Among other things, in designing your information security program, the Safeguards Rule requires your company to:
- Implement and periodically review access controls. Determine who has access to customer information and reconsider on a regular basis whether they still have a legitimate business need for it.
- Know what you have and where you have it. A fundamental step to effective security is understanding your company’s information ecosystem. Conduct a periodic inventory of data, noting where it’s collected, stored, or transmitted. Keep an accurate list of all systems, devices, platforms, and personnel. Design your safeguards to respond with resilience.
- Encrypt customer information on your system and when it’s in transit. If it’s not feasible to use encryption, secure it by using effective alternative controls approved by the Qualified Individual who supervises your information security program.
- Assess your apps. If your company develops its own apps to store, access, or transmit customer information – or if you use third-party apps for those purposes – implement procedures for evaluating their security.
- Implement multi-factor authentication for anyone accessing customer information on your system. For multi-factor authentication , the Rule requires at least two of these authentication factors: a knowledge factor (for example, a password); a possession factor (for example, a token), and/or an inherence factor (for example, biometric characteristics). The only exception would be if your Qualified Individual has approved in writing the use of another equivalent form of secure access control.
- Dispose of customer information securely. Securely dispose of customer information no later than two years after your most recent use of it to serve the customer. The only exceptions: if you have a legitimate business need or legal requirement to hold on to it or if targeted disposal isn’t feasible because of the way the information is maintained.
- Anticipate and evaluate changes to your information system or network. Changes to an information system or network can undermine existing security measures. For example, if your company adds a new server, has that created a new security risk? Perhaps. Because your systems and networks change to accommodate new business processes, your safeguards can’t be static. The Safeguards Rule requires financial institutions to build change management into their information security program.
- Maintain a log of authorized users’ activity and keep an eye out for unauthorized access. Implement procedures and controls to monitor when authorized users are accessing customer information on your system and to detect unauthorized access.
d. Regularly monitor and test the effectiveness of your safeguards. Test your procedures for detecting actual and attempted attacks. For information systems, testing can be accomplished through continuous monitoring of your system. If you don’t implement that, you must conduct annual penetration testing, as well as vulnerability assessments, including system-wide scans every six months designed to test for publicly-known security vulnerabilities. In addition, test whenever there are material changes to your operations or business arrangements and whenever there are circumstances you know or have reason to know may have a material impact on your information security program.
e. Train your staff. A financial institution’s information security program is only as effective as its least vigilant staff member. That said, employees trained to spot risks can multiply the program’s impact. Provide your people with security awareness training and schedule regular refreshers. Insist on specialized training for employees, affiliates, or service providers with hands-on responsibility for carrying out your information security program and verify that they’re keeping their ear to the ground for the latest word on emerging threats and countermeasures.
f. Monitor your service providers. Select service providers with the skills and experience to maintain appropriate safeguards. Your contracts must spell out your security expectations, build in ways to monitor your service provider’s work, and provide for periodic reassessments of their suitability for the job.
g. Keep your information security program current. The only constant in information security is change – changes to your operations, changes based on what you learn during risk assessments, changes due to emerging threats, changes in personnel, and changes necessitated by other circumstances you know or have reason to know may have a material impact on your information security program. The best programs are flexible enough to accommodate periodic modifications.
h. Create a written incident response plan. Every business needs a “What if?” response and recovery plan in place in case it experiences what the Rule calls a security event – an episode resulting in unauthorized access to or misuse of information stored on your system or maintained in physical form. Section 314.4(h) of the Safeguards Rule specifies what your response plan must cover:
- The goals of your plan;
- The internal processes your company will activate in response to a security event
- Clear roles, responsibilities, and levels of decision-making authority;
- Communications and information sharing both inside and outside your company
- A process to fix any identified weaknesses in your systems and controls;
- Procedures for documenting and reporting security events and your company’s response;
- A post mortem of what happened and a revision of your incident response plan and information security program based on what you learned.
i. Require your Qualified Individual to report to your Board of Directors. Your Qualified Individual must report in writing regularly – and at least annually – to your Board of Directors or governing body. If your company doesn’t have a Board or its equivalent, the report must go to a senior officer responsible for your information security program. What should the report address? First, it must include an overall assessment of your company’s compliance with its information security program. In addition, it must cover specific topics related to the program – for example, risk assessment, risk management and control decisions, service provider arrangements, test results, security events and how management responded, and recommendations for changes in the information security program.